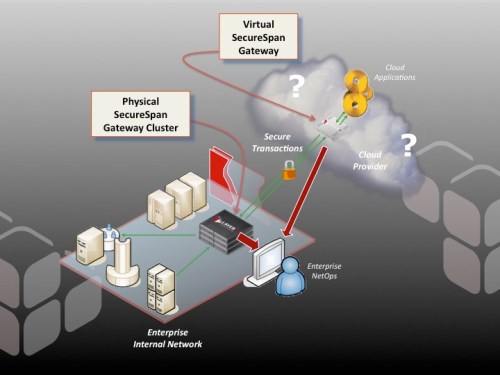
Where does Layer 7 play in the cloud?
Here are the three basic scenarios we see all the time here at Layer 7 with our cloud customers:
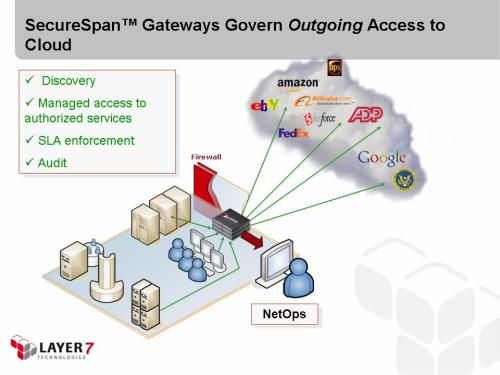
1. Governing Access to External Cloud Apps
Problem: Employees can access cloud services with only a credit card and a browser
Solution: Use Layer 7 SecureSpan Gateway clusters to enforce policy and provide a consistent on-ramp to cloud services.
- Control employee access
- Maintain authoritative usage records
- Provide simple on ramp for cloud services (apply cloud-specific security decorations, etc)
Deployment: Physical appliances for extremely high performance (featuring accelerated cryptography, hardware key management (HSM), and XML processing), software installation on existing server infrastructure, or virtual appliances deployed on commodity hardware. Deploy in clusters for policy synchronization and ease of administration.
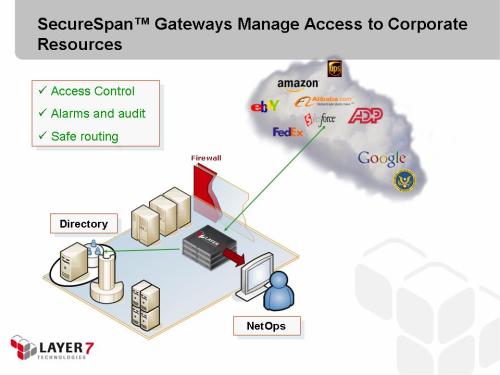
2. Governing Cloud Apps That Need Access to Internal Resources
Problem: Cloud applications (such as Salesforce.com) need access to internal resources (like directories, legacy data bases, mainframes, etc).
Solution: Use Layer 7 SecureSpan Gateway clusters in the DMZ to ensure than only authorized external services (and identities) are permitted access to mission-critical internal systems.
- Authentication
- Fine-grained authorization
- Identity mapping
- Threat detection
- SLA enforcement (for example, throttling access rate to servers)
- Automated internal failover
Deployment: Deploy SecureSpan Gateways in the DMZ to provide secure, managed access to internal network resources. Use hardware appliances for extremely high performance (featuring accelerated cryptography, hardware key management (HSM), and XML processing), software installation on existing server infrastructure, or virtual appliances deployed on commodity hardware. Deploy in clusters for policy synchronization and ease of administration.
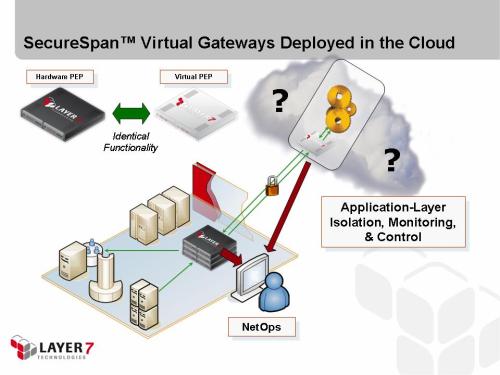
3. Cloud Application Security and Monitoring
Problem: How do you protect cloud applications?
Solution: Use Layer 7 SecureSpan Virtual Appliances to secure and manage all communications in or out of cloud applications.
- Resident in-cloud
- Automatic policy synchronization between other gateways
- Rapid re-deployment and mapping of policy dependencies (IP addresses, etc) within cloud provider, or between cloud providers
- Fine-grained service isolation
- Secure container model or standalone gateway.
Deployment: Hardened and optimized virtual appliances deployed in the cloud. Appliances can be bound to individual machine images, or share responsibility for multiple image instances. Specific virtualized instances for VMWare or Xen-based clouds, or Amazon EC2.
Why Choose Layer 7?
- Experience in Cloud Technology: Layer 7 isn’t just another company jumping on the cloud bandwagon; we’ve been shipping fully supported, productized virtual appliances (not one-offs, nor proof-of-concepts) for over 2 1/2 years. Since the company’s founding in 2002, we have leveraged virtualization technologies. We draw on years of internal expertise in optimizing virtualized images and hardening base operating systems to create a trustworthy application base. SecureSpan is used as the security basis for countless military and intelligence applications. SecureSpan Gateways form the fundamental security infrastructure for the largest cloud project on the planet, which is run by the department of defense.
- True Clustering Solution: Management of outgoing communications cannot become a bottleneck or a single point of failure. Layer 7 is the only vendor in this space that has a real clustering solution for scalability, fault tolerance, and ease of administration.
- Multiple Deployment Options: Hardware appliance, software install, or virtual appliance. Choose what works best for your environment. Mix and match solutions at will.
- Dynamic Policy Download: Layer 7 SecureSpan Gateways can automatically load policies from trusted downstream gateways or central repositories. We pioneered this use case between branch offices and home office, and it extends identically to the cloud
More on this in a following post, including some actual customer deployment scenarios with SaaS providers like Salesforce.com.